|
Quote |
|||
10440 W Pallottine Dr Greenfield, Wl 53228 |
||||
| Bill To | ||||
|---|---|---|---|---|
| Date: | ||||
| # | Descrtiption | Qty | Rate | Amount |
| Sub Total | 0 | |||
| Total | $0 | |||
Notes |
||||
| Looking forward to your business. | ||||
Managed IT Plan Calculator
Cybersecurity
What is a Firewall?
Why Firewall Management is important?
Dark Web
Don't be blindsided by your company's dark web data.
We put security first.
We find what's compromised
What would your employees do?
Remediation with education
But why?
What is Administered Phishing Awareness Campaigns?
X CloseWhat is MDR?
Managed Detection and Response (MDR) denotes outsourced cybersecurity services designed to protect your data and assets even if a threat eludes common organizational security controls. X CloseEnterprise Password Manager
X CloseAdvanced Spam filtration System
X CloseDNS Filtering
X CloseApplication Allowlisting and Ringfencing
X CloseBackup Service
What is Backupify O365 backup?
X CloseWhat is SharePoint Site Backup?
X CloseLocal Server Offsite Backup - Up to 1TB
X CloseWhat is Local Computer Image Based Backup?
X CloseLocal Network
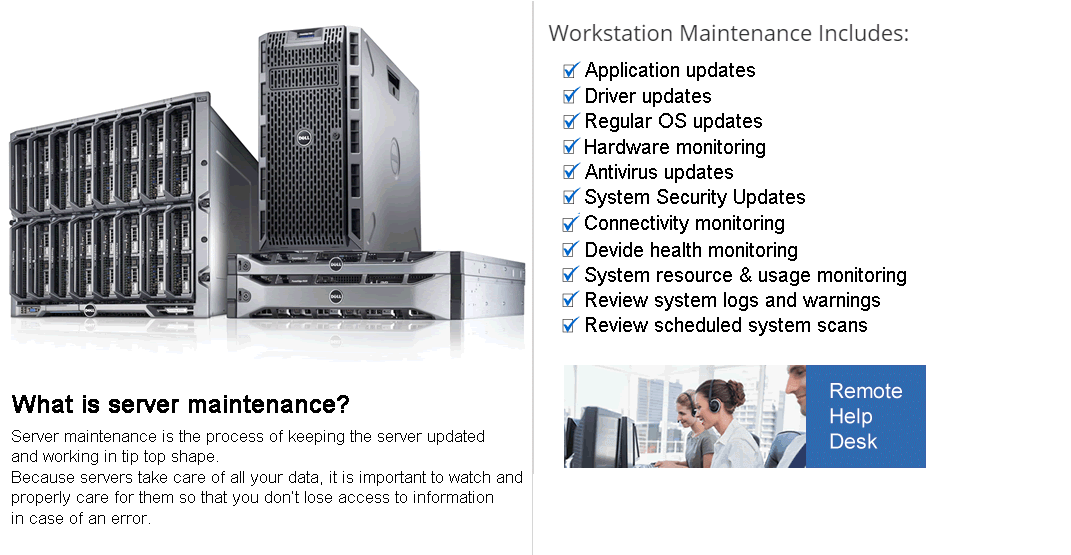
Local Server Maintenance
 X
Close
X
Close
Helpdesk Avalability
Does your company need your IT helpdesk to be available 24 x 7 x 365?
24/7 IT support facilitates resource around the clock. There are many perks of having 24/7 IT helpdesk as your back up. With our 24x7 addon we provide IT helpdesk services 24x7x365, even on public holidays and do not leave you without assistance.
24/7 IT support service achieves the following.
Customer satisfaction at the best
Easy access to technical support
Cost-effective strategy
Unlimited IT Support
Reduced downtime
Multiple communication mediums
Flexibility
Microsoft
Reimagine productivity with Microsoft 365 and Microsoft Teams
Click here to download detailed notes from your new CSO
What is Microsoft 365 Business Premium?
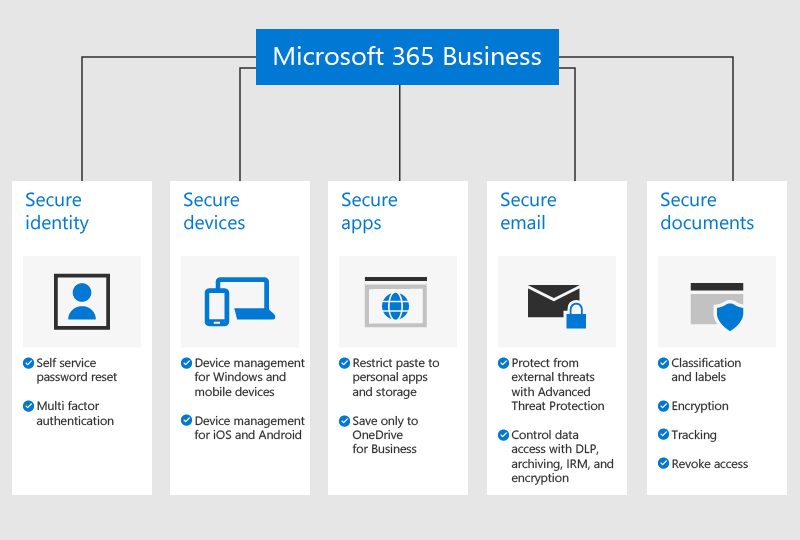 For detailed description please click here. The key components are:
For detailed description please click here. The key components are:
- Microsoft Online Services, including SharePoint, Online Exchange, Teams, OneDrive and many more
- Microsoft Office Applications such as Word, Excel, PowerPoint etc. for Windows, Mac, iOS and Android
- Long-term archiving for exchange, Encryption, In Place & Litigation hold & eDiscovery
- Advanced Threat Protection (ATP), Advanced Information Protection & Data Loss Prevention
- Microsoft EndPoint Manager for connected devices, Intune Mobile Device Management & AutoPilot device deployment
- Simplified deployment with Windows AutoPilot
- Enterprise State Roaming for Windows 10 with Azure AD join
- Help secure and protect your business from the ever-increasing volume of cybersecurity threats out there today.
- Manage your employee’s user accounts, applications, devices and your data in world where your network and applications sprawl well beyond the company firewall.
- Conditional access: Block access to your company resources and data to anyone outside your country.
- Enforce multifactor authentication (MFA) for all your users
- SLA 99.9%
- Simplified device deployments deployment with Windows AutoPilot
- Deploying device profiles and security configuration5
- Windows 10 devices kept up-to-date automatically
- Help protect files and folders on PCs from unauthorized access with Bitlocker
We are happy to answer
your questions.
414-622-1000
IT Helpdesk + Cybersecurity
Monthly Upkeep & Support
Microsoft 365 subscription
Business Premium
Included Services
| Remote Helpdesk And Support | ✓ |
|---|---|
| Helpdesk Hours M-F 9 AM-5 PM | ✓ |
| Line Of Business Apps Technical Support | ✓ |
| Manage Networking | ✓ |
| Dedicated Account Representative | ✓ |
| General Application Updates | ✓ |
| Driver Updates | ✓ |
| Regular Windows Updates | ✓ |
| Hardware Monitoring | ✓ |
| Antivirus Updates | ✓ |
| System Security Updates | ✓ |
| Connectivity Monitoring | ✓ |
| System Resource Monitoring | ✓ |
| Review Scheduled System Scans | ✓ |
| Sharepoint Support/Maintenance | ✓ |
| Dark Web Monitoring | ✓ |
| User Login Logs Are Stored For 30-Days | ✓ |
| Managed Firewall | ✓ |
| Device encryption for company owned desktops and Laptops | ✓ |
| Basic Email Security | ✓ |
| Quarterly IT Reviews | ✗ |
| Weekly System Review And Updates | ✗ |
| Sharepoint Site Backup | ✗ |
| Backupify O365 Backup | ✗ |
| Administered Phishing Awareness Campaigns | ✗ |
| Security - Manage, Detect And Respond - MDR Software. | ✗ |
| Enterprise Password Manager | ✗ |
| User Login Logs Are Stored For Up To 1-Year | ✗ |
| DNS Filtering | ✗ |
| Security Awareness Training | ✗ |
| Advanced Spam Protection | ✗ |
| Identity Security | ✗ |
| Corporate Device Security | ✗ |
| BYOD - Personal Device Security | ✗ |
| Document Security | ✗ |
| Quaterly Device Compliance Review | ✗ |
| Application Allowlisting and Ringfencing | ✗ |
| Advanced Email Security | ✗ |
| Remote Helpdesk And Support | ✓ |
|---|---|
| Helpdesk Hours M-F 9 AM-5 PM | ✓ |
| Line Of Business Apps Technical Support | ✓ |
| Manage Networking | ✓ |
| Dedicated Account Representative | ✓ |
| Quarterly IT Reviews | ✓ |
| General Application Updates | ✓ |
| Driver Updates | ✓ |
| Regular Windows Updates | ✓ |
| Hardware Monitoring | ✓ |
| Antivirus Updates | ✓ |
| System Security Updates | ✓ |
| Connectivity Monitoring | ✓ |
| System Resource Monitoring | ✓ |
| Weekly System Review And Updates | ✓ |
| Review Scheduled System Scans | ✓ |
| Sharepoint Support/Maintenance | ✓ |
| Sharepoint Site Backup | ✓ |
| Backupify O365 Backup | ✓ |
| Dark Web Monitoring | ✓ |
| Administered Phishing Awareness Campaigns | ✓ |
| Security - Manage, Detect And Respond - MDR Software. | ✓ |
| User Login Logs Are Stored For 30-Days | ✓ |
| User Login Logs Are Stored For Up To 1-Year | ✓ |
| Managed Firewall | ✓ |
| Device encryption for company owned desktops and Laptops | ✓ |
| Corporate Device Security | ✓ |
| BYOD - Personal Device Security | ✓ |
| Document Security | ✓ |
| Basic Email Security | ✓ |
| Enterprise Password Manager | ✗ |
| DNS Filtering | ✗ |
| Security Awareness Training | ✗ |
| Advanced Spam Protection | ✗ |
| Identity Security | ✗ |
| Quaterly Device Compliance Review | ✗ |
| Application Allowlisting and Ringfencing | ✗ |
| Advanced Email Security | ✗ |
| Remote Helpdesk And Support | ✓ |
|---|---|
| Helpdesk Hours M-F 9 AM-5 PM | ✓ |
| Line Of Business Apps Technical Support | ✓ |
| Manage Networking | ✓ |
| Dedicated Account Representative | ✓ |
| Quarterly IT Reviews | ✓ |
| General Application Updates | ✓ |
| Driver Updates | ✓ |
| Regular Windows Updates | ✓ |
| Hardware Monitoring | ✓ |
| Antivirus Updates | ✓ |
| System Security Updates | ✓ |
| Connectivity Monitoring | ✓ |
| System Resource Monitoring | ✓ |
| Weekly System Review And Updates | ✓ |
| Review Scheduled System Scans | ✓ |
| Sharepoint Support/Maintenance | ✓ |
| Sharepoint Site Backup | ✓ |
| Backupify O365 Backup | ✓ |
| Dark Web Monitoring | ✓ |
| Administered Phishing Awareness Campaigns | ✓ |
| Security - Manage, Detect And Respond - MDR Software. | ✓ |
| Enterprise Password Manager | ✓ |
| User Login Logs Are Stored For 30-Days | ✓ |
| User Login Logs Are Stored For Up To 1-Year | ✓ |
| Managed Firewall | ✓ |
| DNS Filtering | ✓ |
| Device encryption for company owned desktops and Laptops | ✓ |
| Security Awareness Training | ✓ |
| Advanced Spam Protection | ✓ |
| Identity Security | ✓ |
| Corporate Device Security | ✓ |
| BYOD - Personal Device Security | ✓ |
| Document Security | ✓ |
| Quaterly Device Compliance Review | ✓ |
| Application Allowlisting and Ringfencing | ✓ |
| Basic Email Security | ✓ |
| Advanced Email Security | ✓ |
Managed IT Services - Per User X